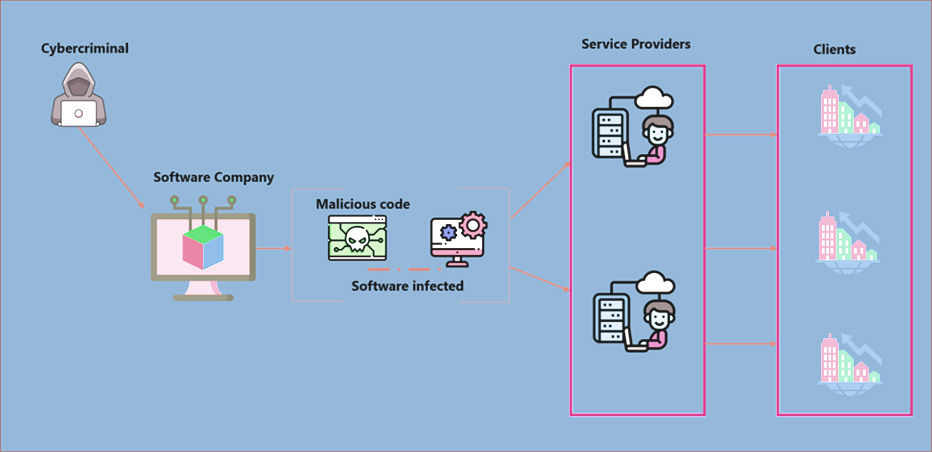
The supply chain attack was unfurling this way. There was an alert to a customer pertaining to a software company. The alert was about a malware trying to deactivate the anti-ransomware and anti-malware features. In another case, cybercriminals targeted the Active Directory (AD), while credential dumping was set in motion in the AD. Had not there been the AI/ML driven proactive monitoring that had been put in place, these supply chain attacks could have wormed their way in and caused harm.
And with new supply chain attack vectors growing by the day, malware hopping from an organization’s network to another, cyberattacks can paralyze the supply chain. The expanding attack surface now demands AI powered automation and security AI to proactively detect, conduct threat hunting, and prevent supply chain attacks; stay one step ahead of the supply chain attack.
What’s Supply Chain attack?
Here’s how a supply chain attack unwinds. At a Payments & Technology company office, a weak spot was spotted by a cybercriminal. And then pushing the malware into the system resulted in the information leak of millions of customers. Here’s an example of how the cyberattack is perpetrated in a supply chain attack.
And to proactively detect and prevent supply chain attacks from causing harm, Extended Detection Response (XDR) helps get a unified view across many attack vectors and establish unified remediation and threat hunting to stop cybercriminals in their tracks.
XDR Approach to Outpace Supply Chain attacks
Security in silos makes it difficult to proactively detect if an attack has been perpetrated. With the XDR method, you can adopt an integrated approach wherein XDR provides that security net over the entire network and serves as the watchtower. XDR advocates collection and correlation of data across networks, email, endpoints, cloud workloads, and servers empowering security teams to proactively detect, analyze, and remediate to prevent data from falling into the hands of cybercriminals.
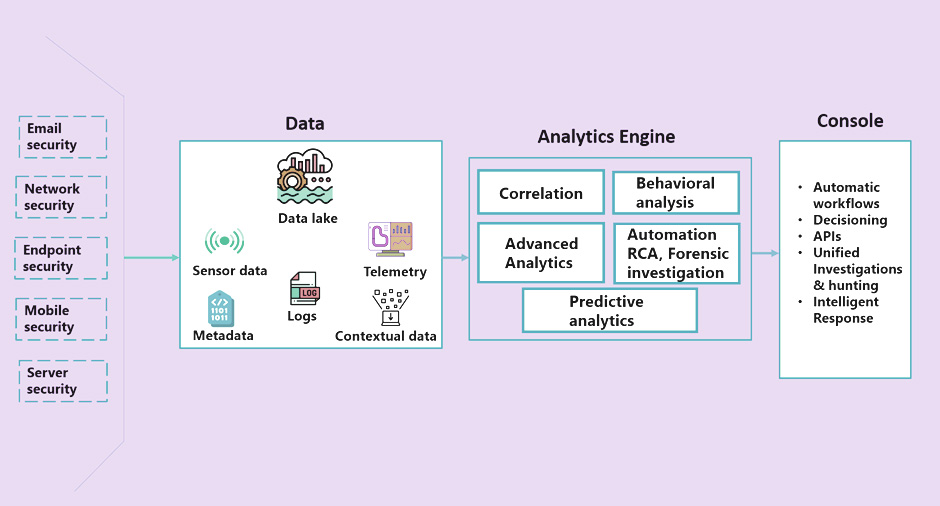
You get a step ahead of the ever-improving cybercriminal. You have a single platform to aggregate data spanning the network infrastructure empowering security teams with visibility, proactive threat detection, continuous monitoring, and automated response. You eliminate blind spots, ensure that data in silos don’t slip through for critical detection. Key features of the XDR approach encompasses:
- Creating a Data lake for saving data pertaining to security tools and facilitating historical analysis
- Facilitating Advanced analytics spearheaded by machine learning to tap into multiple, isolated events and figure out the attack chain
- Promoting a single repository holding event data and analyses guiding investigations
- Enabling correlation of events, proactive monitoring to capture attack signs and roll out actions to prevent it from causing damage
- Conducting behavioral analysis pertaining to entities, user, and machines; You can detect unexpected behaviors, for instance, traffic to one specific location or the traffic from one specific location.
- Enabling assimilation of threat hunting data using the XDR approach leveraged as the baseline for carrying out threat hunting
- Enabling automated root cause analysis and forensic investigations
- Rolling out Prescriptive remediation and orchestrating it
The picture below captures the key features of the XDR approach that empowers organizations with unified data visibility as well as unified analytics to be proactive in outsmarting fast-paced attacks.
Embracing the XDR approach, advanced threats can be detected quickly, as that of malicious insiders and compromised credentials, time-to-answers get reduced wherein security teams can visualize recommendations regarding remediation. Most importantly, XDR approach spearheaded by advanced analytics, ML and AI helps gain contextual insights around an attack.
As Software supply chain attacks grow in number, it is now imperative to adopt a proactive approach to thwart attacks, with the re-invigorated AI/ML powered security empowering organizations to up their game and mitigate supply chain attacks.